Welcome to our August 2023 catches of the month feature, in which we explore the latest phishing scams and the tactics that cyber criminals use to trick people into handing over personal data.
This month, we have a pair of stories about Microsoft. The first looks at an alarming rise in phishing scams that impersonate the tech firm, while the second discusses a new security feature that’s designed to protect users from password compromise.
Microsoft becomes the most mimicked phishing brand
Phishing scams involving Microsoft have soared in the past three months, according to research from the security firm Check Point.
The tech giant has always been a popular target for crooks, but analysts claim that its brand has become the most frequently used in email scams, up from third place at the start of the year.
Check Point credits this rise to an extensive phishing campaign that told victims that there has been suspicious activity on their Microsoft account.
These types of scams have proven wildly successful, because the majority of Internet users have a Microsoft account for either personal purposes or for their job.
The pretext is also a quintessential example of phishing, as it creates a sense of shock and urgency. Recipients are liable to panic if they think that someone is trying to break into their account, and follow the link instantly without checking for the usual signs of a scam.
Microsoft has long been aware of these schemes, and its help page contains warnings and examples to help users stay safe.
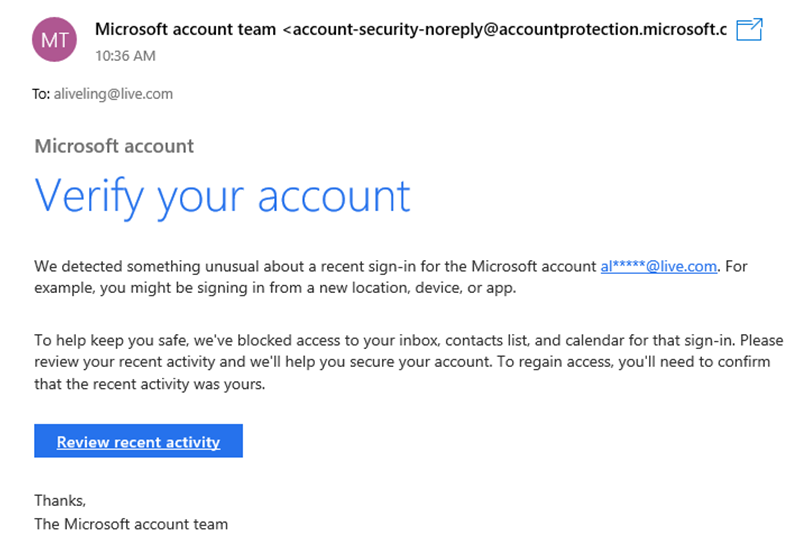
Source: Microsoft
The messages faithfully recreate the layout of a genuine Microsoft email, and tell recipients that the organisation has “detected something unusual about a recent sign-in for the Microsoft account [email address]. For example, you might be signing in from a new location, device, or app”.
It adds that it has frozen the account, and to regain access users must follow a link – which is conveniently hidden in a button to mask its true destination.
Although the ultimate URL will change depending on the campaign, given that fraudulent sites are usually shut down after a few days – or even hours – they will typically display as a facsimile of the Office 365 login page.
Users who attempt to log in via this page are unwittingly handing their credentials to the cyber criminals who control the page. After they hit enter, the page will either run into a supposed error or will redirect them to the genuine Office 365 login page to avoid arousing suspicion.
Windows 11 bolsters its phishing protection features
As phishing attacks against Microsoft increase, the tech firm has hit back by enhancing the security practices on its Windows 11 operating system.
This comes in the form of a new feature in its Enhanced Phishing Protection tool, which was released as part of Windows 11 22H2.
The tool is designed to protect users’ Windows and Active Directory domain credentials from being stolen by threat actors.
One of the ways it does that is by warning people about security threats when they enter their Windows password into websites and documents.
Previous versions of the tool did this when users manually typed their passwords onto websites, but analysts noted that many people copy and paste their credentials, which inadvertently bypassed its security protections.
As a result, a new version of its Enhanced Phishing Protection tool – released as part of Windows 11 Insider Dev build 23506 – now includes a feature that detects when users copy and paste their Windows login credentials.
The feature is not enabled by default, so anyone who wants to make use of it should adjust their system settings on the Windows Security panel.
Once it’s enabled, users will receive a security alert when they type or copy their login credentials into website forms or documents.

Source: BleepingComputer
The alert reads: “If your password is stolen from this site, attackers will try to use it at other sites too. Use strong, unique passwords to keep your personal information safe.
“Microsoft recommends changing your local Windows account password.”
Can you spot a scam?
All organisations are vulnerable to phishing, no matter their size or sector, so it’s essential to understand how you might be targeted and what you can do to prevent a breach.

You can help educate your staff with IT Governance’s Phishing Staff Awareness Training Programme.
This 45-minute course uses real-world examples like the ones we’ve discussed here to explain how phishing attacks work, the tactics that cyber criminals use and how you can detect malicious emails.
