Phishing attacks are among the most common forms of cyber crime that organisations face, so it’s crucial that you learn how to prevent scams.
According to a Digital Guardian report, 90% of data breaches are caused by phishing, while Venari Security found that organisations lose approximately $181 (£150) for each piece of personal information stolen in online scams.
But what can organisations and individuals do to ensure that they don’t fall victim? We answer that question in this blog, as we provide our top ten ways to avoid phishing attacks.
1. Be cautious when clicking on links or downloading attachments
Scammers can use any number of pretexts to trick people into falling for their traps. Some bogus messages might look like security alerts, for instance, whereas others advertise bargain discounts at an online retailer.
No matter what form these messages take, they are designed to fool you into clicking malicious links or downloading malware-infected attachments.
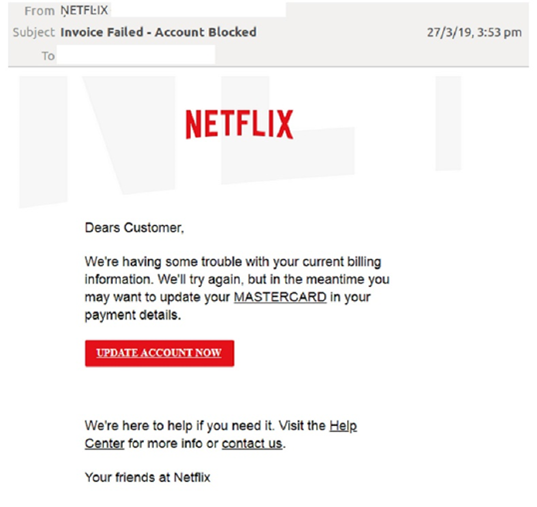
In this example, seen by MailGuard, the message appears to be a security alert from Netflix.
You should therefore be careful when you receive an email instructing you to follow a link or download an attachment.
That’s not to say every message with a link or an attachment is fraudulent. There are, of course, plenty of legitimate reasons why someone might send you one of these things. However, these are the clearest and most consistent signs that something might be amiss.
If you see such a request, you should consider it a warning and look for other clues associated with phishing emails.
2. Use multi-factor authentication
In many phishing scams, the attacker’s motive is to capture the victim’s passwords in order to compromise their account. This is often the case with their two most popular techniques – bogus links and attachments – which we discussed in the previous section.
Whereas a bogus link might ask the user to provide their login details directly, bogus attachment usually work by unleashing a keylogger, which is a type of malware that tracks what is being typed on a device and is typically used to capture login credentials.
No matter how strong your password is, it will mean nothing if you inadvertently hand it over to scammers.
This is one of the reasons that MFA (multi-factor authentication) has become so important. The process adds a second layer of security to the login process, with users required to provide a second piece of information in addition to a password.
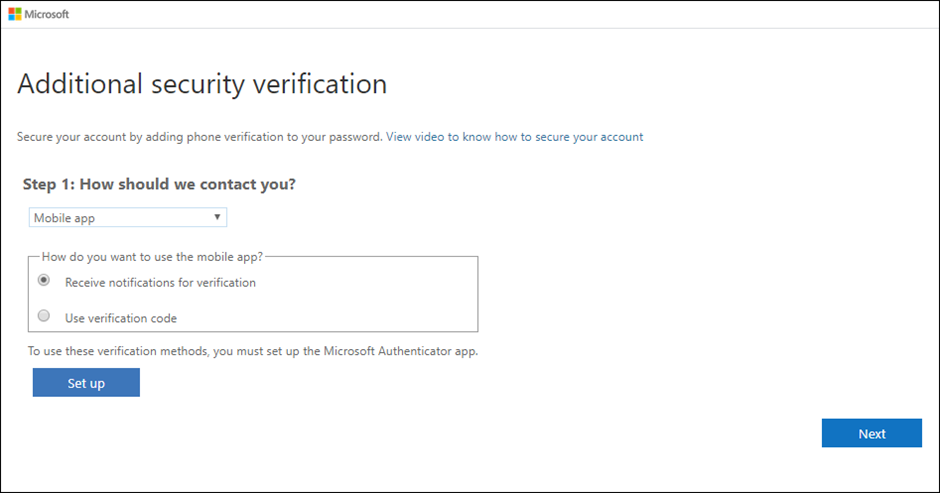
A typical MFA system will prompt you to receive a second set of credentials after entering your password.
The most common additional factor is an OTP (one-time password) sent to the users’ phone or email address. Elsewhere, some systems use hardware tokens, which are USB-like devices that produce OTPs, while others authenticate people with biometric data, such as fingerprint scans or facial recognition software.
Hardware tokens and biometric data are more secure options, because they require the physical asset – whether it’s a device or the person’s body itself – to log in.
However, they are expensive to set up, and with biometric data in particular, organisations are required to collect and process highly sensitive information that can pose extreme risk if exposed.
When you’re setting up MFA, you should consider which authentication method best balances the user’s security with your own information security risks.
3. Use antivirus and anti-malware software
Software solutions, such as antivirus and anti-malware programmes, provide an essential defence in preventing phishing.
They do two crucial things in the fight against scams. First, most programmes will include clear warnings whenever an email contains an attachment from an unknown sender, reminding them that the file could contain malware.
Even if the user ignores this advice and opens the attachment, the software will scan the file for anything suspicious.
It’s no surprise, therefore, that antivirus and anti-malware software are some of the most common cyber security tools for both organisations and individuals.
There are a variety of products available, and although paid programmes have historically been widely popular, many operating systems now include in-build antivirus tools, such as Windows Defender, which are increasingly adept at rooting out scams.
4. Learn about the latest trends
One of scammers’ favourite techniques is create phishing pretexts based on current events. For example, there is always an influx of phishing attacks imitating HMRC or the IRS during tax season.
Scammers also capitalise on news stories or popular events, from sports contests to election campaigns, as baits for their scams.
By using things that are already on people’s minds, the criminals lend their attacks a sense of legitimacy.
People are less likely to think of it as an unsolicited email that’s appeared as if from nowhere, and might even subconsciously make connections between this email and previous discussions of the topic from trusted sources.
Thankfully, people are quick to share such scams with the public to raise awareness and prevent others from falling victim. IT Governance does its part in this, as we share a collection of the latest phishing trends in our catches of the month feature.
We recommend that you keep an eye out for alerts such as these, so you can stay one step ahead of the attackers.
5. Use a password manager
Weak passwords are among the biggest – and most avoidable – mistakes that people make in the fight against phishing. In particular, people’s habit of reusing the same password on multiple accounts exposes them to significant risk.
That’s because cyber criminals’ goal with phishing emails is, in many cases, to capture your login credentials. A typical scam will redirect you to a bogus website, where you’re asked to hand over your username and password.
But the attackers aren’t only interested in your credentials for that one site. They’ll reuse the password elsewhere – usually on more sensitive accounts, such as online banks or other websites where you store payment card data or other valuable information.
To combat this, people must get into the habit of using unique passwords for their accounts. It can be tricky to remember countless different sets of credentials (one of the reasons we reuse passwords so often), but the task is much easier with the help of a password manager.
These systems can create complex, unique passwords for any account you like, and you can store the information on their systems to ensure that you never forget your credentials.
6. Don’t share sensitive information
A mistake that’s even more avoidable than reusing passwords is sharing them with other people. There are several circumstances where you might be tempted to do this, and the individual might assume that they can trust the other person, but it defies the very purpose of having a password and can create serious problems.
Say, for instance, a colleague emails you about the new software system your organisation has just implemented. There’s only have one licence so far, and it’s been put in your name, but now your colleague is requesting access so that they can work on it.
You might think that there’s nothing harmful in complying with their request. After all, you don’t want to obstruct them in trying to do their job, and you certainly don’t want to be blamed for a project being delayed because you wouldn’t cooperate.
However, you are responsible for the activity that happens on that account. If your colleague makes a mistake and a data breach ensues, you will be at fault.
Even more worryingly, you might find that the request didn’t come from your colleague at all but a scammer who had compromised or otherwise imitated their account. By sharing your password, you have given them free access to the system and allowed them to can wreak havoc.
The lesson is that you should never share your password under any circumstance. They are unique to your accounts, and you are the only person who should do anything on them.
If the person contacting you has a legitimate reason to use that system, you should either perform the task on their behalf or tell them to contact someone who can set them up with their own login access.
7. Enable spam filters
Spam filters are another useful tool to help individuals identify phishing emails. As with antivirus and anti-malware software, they alert people to suspicious emails from untrustworthy senders.
Most spam is relatively harmless, and emails are generally designed to clog up inboxes rather than dupe recipients. Most people can spot them thanks to their crude and sometimes lurid messages.
However, spam filters are designed to block a variety of malicious emails, including more sophisticated phishing scams that might be harder to spot.
8. Be cautious of unsolicited phone calls or text messages
Although phishing is generally associated with email, cyber criminals can target people in many other ways. Two common variations use telephones, with scammers targeting people with both malicious phone calls (‘vishing’) and text messages (‘smishing’).
Phone calls are especially dangerous, because they require a great deal of confidence to pull off, and anyone who does so successfully can lure targets in with great proficiency. We tend to be more susceptible to requests to requests when they’re delivered directly rather than in writing.
Likewise, scammers often exploit the sense of urgency that’s created with a phone call. Whereas you can come back to an email at a time that suits you, phone calls create a sense of pressure to complete the request immediately.
This gives you less time to assess what the other person is requesting and whether it sounds legitimate, and makes it harder to consult a third party for advice.
By contrast, smishing scams exploit the lack of information and urgency that the text message format provides. Unlike either bogus phone calls or email addresses, where the scammer goes to great lengths to replicate the style and form of a genuine correspondence, SMS messages are much more basic.
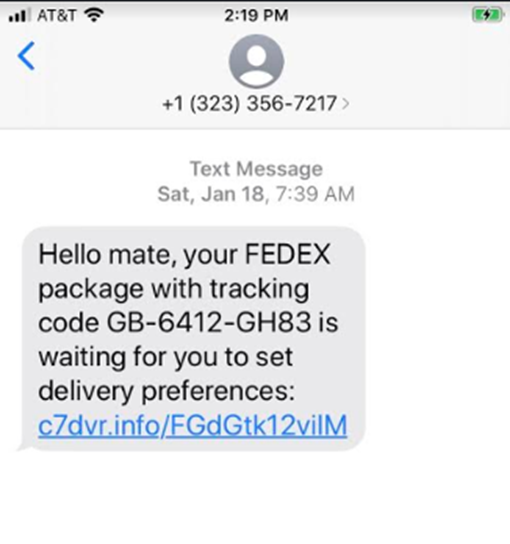
In this example, seen by Proofpoint, the scammer includes a link to a bogus website.
Scammers thrive in these situations, because even legitimate messages comprise little more than a phone number, a brief message and a shortened URL. It’s therefore much easier for crooks to replicate the real thing and lure people in.
To prevent smishing attacks, you must be extremely careful whenever you receive an unsolicited text message that requests that you take action. The message might ask you to follow a link, as in the example above, or it might simply ask you to respond to test how susceptible you are to their bait.
If you’re in any doubt whether a message is genuine, find a trusted contact number for the organisation in question and ask them to verify the legitimacy of the request.
9. Regularly review your bank statements
Like most criminals, scammers’ main objective is to make money. Although they often do this by stealing and selling sensitive information, they often take a more direct approach and attempt to compromise victims’ payment card information.
You might not always be able to prevent this from happening. Scams are increasingly sophisticated, and even if you don’t become the victim yourself, an organisation that holds your data might be compromised.
Thankfully, it’s relatively easy to catch scammers in the act and mitigate the damage. All you have to do is review your bank statements and recent transactions and look for large transactions from your account that you didn’t make.
Scammers often try to launder the stolen money by hiding its source. One of their most popular techniques is to purchase online gift cards, and then return the items instore to get a refund.
If you check your bank accounts regularly, you can spot these sorts of fraudulent activities promptly and freeze the compromised accounts.
10. Staff awareness training
In an organisational context, there is no better way to prevent phishing attacks than staff awareness training. Your employees are your last line of defence, and the security of your data is ultimately a matter of how they respond to phishing emails.
We’ve discussed several tools that can help them, from antivirus software and spam filters to password managers and two-factor authentication, but they are only effective if the person using them acts responsibly.
Employees must recognise the threat that phishing poses and be capable of spotting a malicious message. Likewise, they must be familiar with the organisation’s information security policy and heed the guidance that you give them.
IT Governance understands the importance of staff awareness training and is a premier provider of information security e-learning modules.
We can help you and your team tackle the threat of scams with our Phishing Staff Awareness Training Programme.

This 45-minute course was developed by experts and uses real-life examples that bring to life the threat of phishing and the techniques that cyber criminals use.
Thanks to our interactive learning and online assessment tools, you can be sure that staff engage with and understand what’s required of them to protect their sensitive information and avoid data breaches.